Strong passwords are one of the few controls that directly block attackers. WordPress, however, prioritizes usability over strict enforcement: it recommends strong passwords but still allows weak ones if a user confirms the choice. If you want real, enforceable rules, you’ll need a third-party plugin such as WP Password Policy. Below is the breakdown of what WordPress does by default, where it falls short, and how to fix it properly.
What WordPress Actually Requires
Out of the box, WordPress does not require strong passwords. When a user sets or changes a password, WordPress displays a strength meter. If the meter says “Weak,” the user can still proceed by ticking “Confirm use of weak password.” That’s it. There is no minimum length requirement, no enforced complexity, no role differentiation, and no built-in expiration. The strength meter is guidance – not a gate.
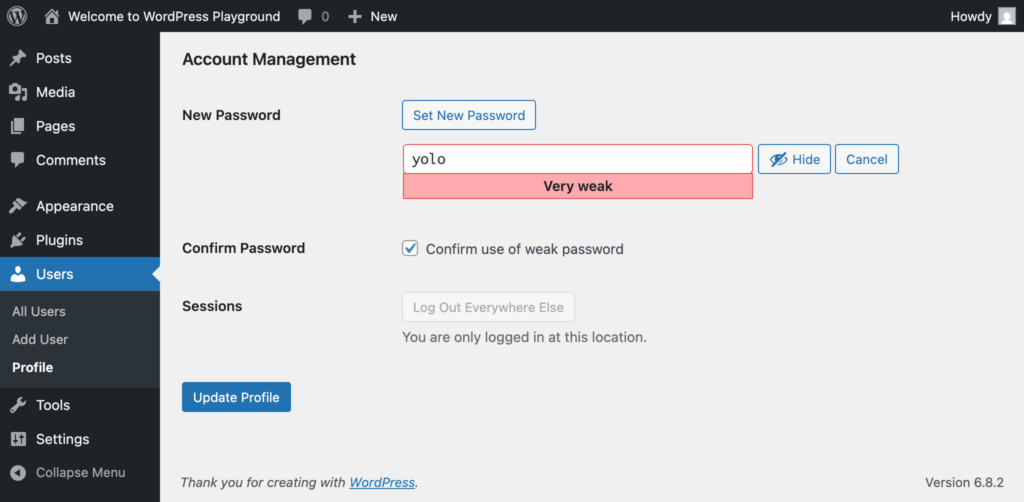
How the Strength Meter Works (and Why It’s Only Guidance)
The meter uses the zxcvbn library to estimate how hard a password is to guess. It considers length, character variety, obvious patterns (dictionary words, dates, keyboard sequences), and known leaks. This is helpful education for users, but it’s advisory only. If someone wants to keep “Summer2025” or “password123”, WordPress will let them do it with a single checkbox – even when the meter clearly flags it as weak.
Why the Default Isn’t Enough
Security-wise, the defaults leave large gaps. Weak passwords can still be used, which immediately undermines protection against brute force and credential stuffing. There’s no way to demand different standards for high-privilege users, and nothing requires rotation or prevents reuse. In teams, agencies, shops, or membership sites, that’s a liability: the most sensitive accounts are not held to a higher bar, and compromised credentials can persist indefinitely.
➡️ In plain terms: WordPress recommends; it does not enforce. That’s fine for hobby sites, but not acceptable for anything with revenue, reputation, or data risk on the line.
Enforcing Real Requirements with WP Password Policy
If you want enforceable rules, you need a plugin. WP Password Policy turns recommendations into hard requirements you control. You can set a minimum length that actually blocks saves below that threshold; require specific character classes; define blocked words or patterns; and apply stricter rules to admins than to subscribers. It also supports password expiration and history so users can’t recycle the same weak credential forever.
Because it integrates with popular ecosystems like WooCommerce and Ultimate Member, the rules apply consistently across registration, login, and password-change flows. In short: it fixes the enforcement gap that WordPress leaves open.
Recommended Policy Settings for 2025
For most production sites, a sensible baseline looks like this:
- Minimum length: at least 12 characters (16+ for admin-level accounts).
- Composition: require a mix of uppercase, lowercase, numbers, and symbols, while blocking obvious words and leaked patterns.
- Role-based rules: enforce stricter policies for administrators, editors, shop managers, and anyone with write access to code or content at scale.
- Expiration and history: rotate high-privilege credentials periodically and prevent reuse of recent passwords.
- 2FA (separate control): pair strong passwords with two-factor authentication for privileged users.
These aren’t theoretical niceties. They directly shrink the attack surface and reduce the blast radius of inevitable credential leaks elsewhere.
Quick Comparison: Default vs. Enforced
| Area | Default WordPress | With a WP Password Policy plugin |
|---|---|---|
| Minimum length | Not enforced | Enforced (your value) |
| Complexity | Not enforced | Enforced (you choose the rules) |
| Weak passwords | Allowed with a checkbox | Blocked |
| Role-based standards | Not available | Per-role policies |
| Expiration & history | Not available | Built in |
| Plugin ecosystem coverage | Inconsistent | Enforced in supported flows (e.g., WooCommerce, Ultimate Member) |
Bottom Line
WordPress only recommends strong passwords. It will still accept weak ones if a user insists. If you’re serious about security, you need enforcement, not advice. A plugin such as WP Password Policy lets you define and apply real requirements – per role, across key user flows, with expiration and history – so weak credentials never slip through.
FAQs
Does WordPress require strong passwords by default?
No. WordPress uses a strength meter to recommend strong passwords, but users can still choose weak ones if they confirm their choice.
Can I set a minimum password length in WordPress?
Not without a plugin. By default, WordPress has no enforced minimum length.
How can I force users to create strong passwords in WordPress?
Use a plugin like WP Password Policy to set length, complexity, role-based rules, and expiration.
Does WP Password Policy work with WooCommerce or membership plugins?
Yes. It integrates with WooCommerce, Ultimate Member, and other plugins to enforce your policy during registration, login, and password changes.